What Is IoT Monitoring?
IoT monitoring refers to the continuous observation, analysis, and interpretation of data generated by connected devices in order to understand how an entire system behaves over time. Unlike traditional monitoring, which often focuses on predefined metrics or individual components, IoT monitoring operates at the system level, correlating telemetry across devices, gateways, networks, and data pipelines.
In practical terms, IoT monitoring answers questions such as whether data is arriving on time, whether patterns across devices are changing, and whether the system is still operating within expected boundaries. It combines real-time data ingestion, scalable storage, analytical querying, and alerting to support operational awareness and decision-making in environments where devices are numerous, distributed, and often unreliable.
Key idea: IoT monitoring is not about collecting device data—it is about continuously understanding system behavior under real-world conditions.
IoT Monitoring vs. IoT Device Monitoring
Although the terms are often used interchangeably, IoT monitoring and IoT device monitoring solve fundamentally different problems.
| Dimension | IoT Device Monitoring | IoT Monitoring |
|---|---|---|
| Primary focus | Individual device health | System-level behavior |
| Typical metrics | Connectivity, battery, firmware | Data flow, latency, anomalies |
| Scale | Dozens to thousands | Thousands to millions |
| Main users | Operations, field engineers | Platform, data, and SRE teams |
| Key question | “Is this device alive?” | “Is the system behaving as expected?” |
IoT device monitoring focuses on the state of individual devices. Typical concerns include whether a device is online, how much battery it has left, whether a sensor is responding, or whether firmware updates have succeeded. This type of monitoring is essential for day-to-day operations and troubleshooting, especially during deployment and maintenance phases.
IoT monitoring, on the other hand, is concerned with system-wide behavior. It looks beyond single devices to answer questions such as whether data streams are delayed, whether anomalies are emerging across regions or cohorts, or whether the system is drifting away from expected performance patterns. At this level, a single device failure is often less important than correlated changes across thousands of devices.
From an engineering standpoint, the distinction becomes clear at scale:
- Device monitoring detects local failures
- IoT monitoring detects systemic issues
Most production IoT systems require both. Device monitoring keeps the fleet alive; IoT monitoring ensures the system continues to function as intended as complexity, scale, and data volume increase.
When IoT Monitoring Is Needed (And When It’s Not)
You need IoT monitoring when understanding system behavior becomes more important than checking individual devices. If you can no longer answer operational questions by inspecting a single device or dashboard, you are likely dealing with a system-level monitoring problem.
You likely need IoT monitoring if:
- You manage hundreds or thousands of devices across locations
- Your system depends on continuous data streams, not periodic reports
- You need to detect patterns, trends, or anomalies, not just outages
- Data delays, drops, or inconsistencies have real operational impact
- Diagnosing issues requires correlating signals across many devices
In these scenarios, device-level monitoring alone cannot provide sufficient visibility into how the system behaves as a whole.
You may not need full IoT monitoring if:
- Your deployment is small and centrally managed
- Devices report data infrequently and reliably
- Failures are obvious, local, and easy to diagnose
- Most issues can be resolved by checking individual device status
In such cases, basic device monitoring and simple alerting are often easier to operate and more cost-effective.
How IoT Monitoring Works
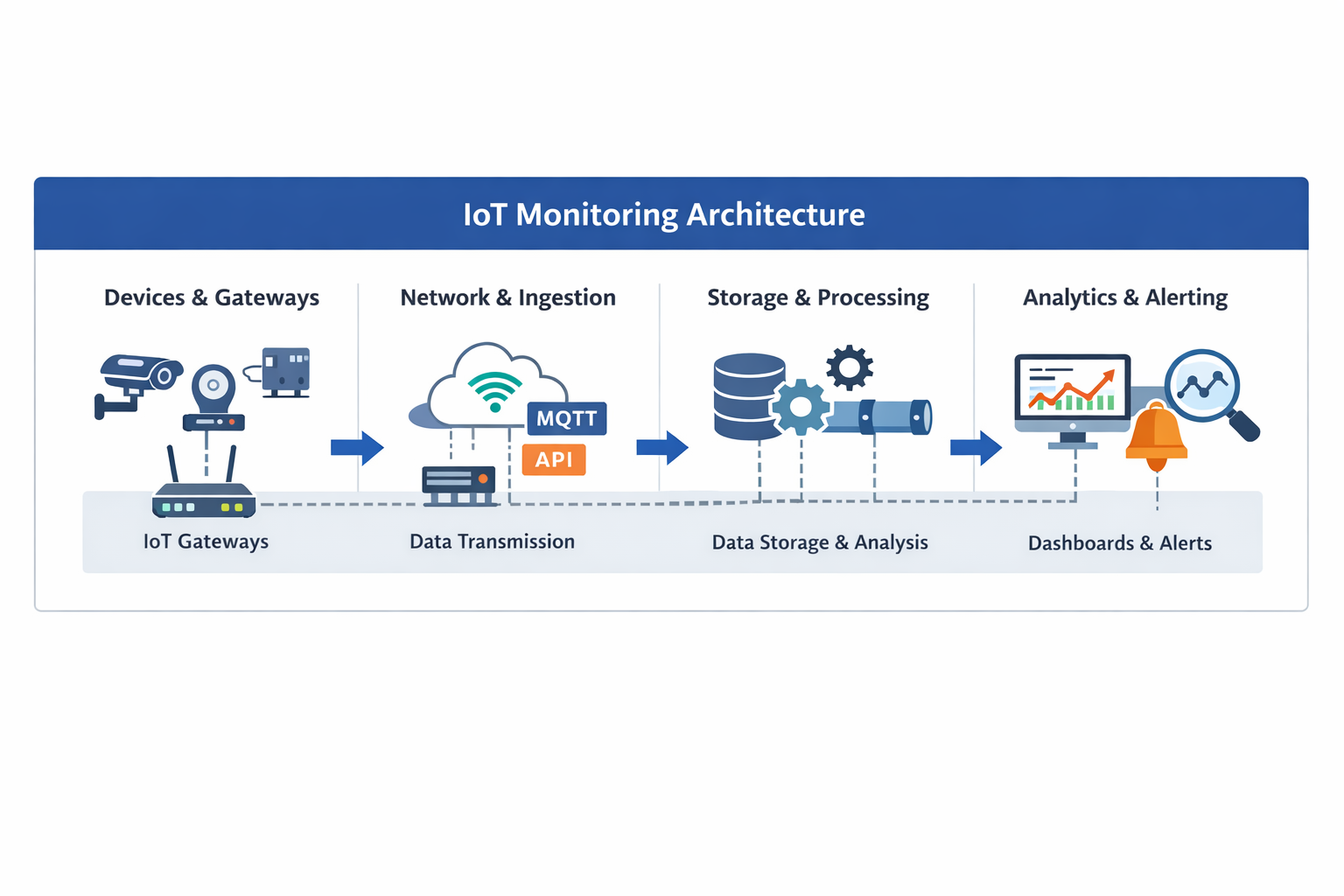 At a high level, IoT monitoring is not a single component but an end-to-end system that spans from physical devices to analytical workflows. Each layer introduces its own constraints—network reliability, data volume, latency, and operational complexity—and monitoring only works when these layers are designed to work together rather than in isolation.
At a high level, IoT monitoring is not a single component but an end-to-end system that spans from physical devices to analytical workflows. Each layer introduces its own constraints—network reliability, data volume, latency, and operational complexity—and monitoring only works when these layers are designed to work together rather than in isolation.
The following architecture reflects how IoT monitoring systems are typically built and operated in production environments.
Device & Gateway Layer (Including IoT Gateway Monitoring)
The foundation of any IoT monitoring system is the device and gateway layer. Devices generate raw telemetry—such as temperature, vibration, location, or power state—often under constrained conditions like limited CPU, memory, or battery life.
Gateways sit between devices and backend systems and serve multiple roles:
- Aggregating data from large numbers of devices
- Performing basic filtering or preprocessing
- Buffering data during network outages
- Translating protocols between devices and cloud services
From a monitoring perspective, gateways are critical failure points. A single gateway issue can manifest as hundreds or thousands of “offline” devices, even though the devices themselves are healthy. As a result, effective IoT monitoring must treat gateways as first-class entities, tracking connectivity, throughput, error rates, and backpressure—not just device heartbeats.
This is why gateway monitoring is less about choosing a single “best tool” and more about ensuring visibility into how edge components behave under real-world conditions.
Data Ingestion & Transmission
Once data leaves the edge, it enters the ingestion and transmission layer. IoT systems typically rely on asynchronous, event-driven communication to cope with unreliable networks and uneven traffic patterns.
Common approaches include:
- MQTT, for lightweight publish/subscribe messaging
- RESTful APIs, for configuration and control paths
- Satellite IoT, for environments without terrestrial connectivity
From an IoT monitoring standpoint, ingestion is not simply about accepting data. The system must handle:
- Bursty traffic caused by reconnecting devices
- Duplicate or out-of-order messages
- Long gaps followed by delayed data delivery
Monitoring ingestion pipelines often reveals systemic issues before devices appear to fail. Rising ingestion latency, increasing retry rates, or growing backlogs are early indicators that the system is under stress.
Data Storage & Processing (Why Scale Is Hard in IoT)
At scale, IoT monitoring becomes a data engineering problem as much as a monitoring one.
IoT data exhibits:
- High cardinality (millions of device IDs, locations, attributes)
- Continuous writes with limited opportunities for batching
- Evolving schemas as devices and firmware change over time
Traditional monitoring systems are usually optimized for low-cardinality metrics and short retention periods. IoT monitoring systems must instead support large, append-heavy datasets while still enabling fast queries across time, device groups, and dimensions.
From an engineering standpoint, modern IoT monitoring closely resembles observability systems, with one key difference: the telemetry originates from physical devices rather than software services. Physical constraints—such as intermittent connectivity and delayed delivery—make storage and processing design decisions especially critical.
Analytics, Visualization, and Alerting
The final layer of IoT monitoring turns raw telemetry into actionable insight.
At small scale, static dashboards and simple threshold-based alerts may be sufficient. At larger scales, these approaches quickly break down. Normal behavior often varies by device type, location, or time of day, making fixed thresholds noisy and unreliable.
Effective IoT monitoring systems emphasize:
- Real-time and near-real-time analytical queries
- Support for late-arriving data without invalidating results
- Pattern- and trend-based anomaly detection rather than single-point alerts
Visualization and alerting are important, but they sit on top of the analytics layer. Without the ability to explore data interactively and correlate signals across dimensions, dashboards become passive displays rather than tools for understanding system behavior.
Types of IoT Monitoring Applications
While the core principles of IoT monitoring remain consistent, the way they are applied varies significantly depending on the environment, data characteristics, and operational constraints. Different use cases place different demands on devices, networks, and analytics systems, which in turn shapes how monitoring is designed and operated in practice.
The following examples illustrate some of the most common IoT monitoring application patterns seen in real-world deployments.
Industrial & Manufacturing IoT Monitoring
In industrial environments such as paper mills, IoT monitoring often begins with a narrow operational goal and expands over time.
A typical implementation path looks like:
- Instrument critical machines with sensors
- Stream telemetry to a central system
- Correlate signals across production stages
- Detect inefficiencies or early signs of failure
The technical challenge is rarely data collection—it is correlating and analyzing signals across machines, processes, and time.
Environmental & Temperature Monitoring
Environmental monitoring focuses on continuous measurement of conditions such as temperature, humidity, and air or water quality.
Deployments typically involve large numbers of low-power sensors sending sparse updates. Monitoring systems must handle noisy data, long retention periods, and cost constraints while still supporting trend analysis and alerts.
Remote & Satellite IoT Monitoring
Satellite IoT enables monitoring in environments without terrestrial connectivity, such as mines, oceans, or pipelines.
These systems operate under strict constraints:
- High latency
- Limited bandwidth
- Expensive transmissions
Monitoring platforms must tolerate delayed and incomplete data while still providing meaningful insights.
Key Benefits and Trade-offs of IoT Monitoring
From an engineering and operational perspective, IoT monitoring is rarely adopted for a single reason. Teams invest in it because it changes how systems are operated over time—but those benefits only materialize when the associated trade-offs are clearly understood. Evaluating IoT monitoring therefore requires looking at both what it enables and what it costs to run and maintain at scale.
Key Benefits
System-level visibility is the most immediate benefit of IoT monitoring. Instead of reacting to individual device failures, teams gain a continuous view of how fleets behave across time, geography, and operating conditions. This makes it possible to identify systemic issues that would otherwise remain hidden behind isolated alerts.
Predictive maintenance becomes feasible once historical and real-time telemetry can be analyzed together. Rather than relying on fixed maintenance schedules or reactive repairs, teams can detect early warning signals—such as gradual drift or correlated anomalies—and intervene before failures occur.
Cost optimization emerges as a secondary but significant benefit. With better visibility, organizations can reduce unplanned downtime, optimize energy usage, and avoid over-provisioning infrastructure. In large deployments, even small efficiency gains can translate into meaningful cost savings.
Just as importantly, IoT monitoring improves decision-making under uncertainty. When systems operate in dynamic environments, having timely and trustworthy data allows teams to make informed trade-offs instead of relying on assumptions or incomplete signals.
Trade-offs and Limitations
The benefits of IoT monitoring come with non-trivial trade-offs that are often underestimated during early design stages.
Latency is a fundamental consideration. Real-time or near-real-time insight requires continuous data ingestion and processing, which introduces architectural complexity and operational overhead. Systems designed for batch analysis often struggle to meet these requirements.
Data cost grows quickly as device counts and data retention periods increase. Storage, compute, and network costs must be balanced against the value of the insights produced. Without careful data modeling and retention strategies, monitoring pipelines can become expensive to operate.
Operational complexity is another significant factor. IoT monitoring systems span devices, gateways, networks, ingestion pipelines, storage engines, and analytics layers. Each component introduces new failure modes, and maintaining reliability across the entire stack requires specialized expertise.
False positives and alert fatigue are common failure modes. Noisy signals, environmental variability, and poorly tuned alerts can overwhelm operators, reducing trust in the monitoring system itself. Effective IoT monitoring requires ongoing calibration and an emphasis on trend-based analysis rather than static thresholds.
In practice, successful teams treat these trade-offs as design constraints rather than afterthoughts, building systems that balance insight, cost, and operational effort from the outset.
Challenges in IoT Monitoring at Scale
As IoT systems scale from pilot deployments to production environments, monitoring challenges shift from isolated technical issues to systemic constraints. At large scale, data characteristics, security risks, and alerting behavior interact in ways that traditional monitoring approaches are not designed to handle.
Below are the most common challenges teams encounter when operating IoT monitoring systems at scale.
High Data Volume, Velocity, and Variety
IoT monitoring systems must handle extreme data scale across multiple dimensions at once.
At large deployments, millions of devices generate continuous streams of telemetry, resulting in:
- High volume: sustained ingestion of time-series and event data
- High velocity: bursty traffic patterns caused by reconnects or synchronized reporting
- High variety: heterogeneous payloads and evolving schemas across device types and firmware versions
The primary challenge is not data ingestion, but efficient querying and correlation across time, devices, and dimensions. Systems optimized for low-cardinality metrics often struggle once device IDs, locations, and attributes scale into the millions.
Key takeaway: IoT monitoring breaks down when data systems cannot efficiently query high-cardinality, real-time telemetry.
Security and Firmware Risks
Security challenges in IoT monitoring are structural, not incidental.
IoT devices are often deployed in uncontrolled or remote environments, making them difficult to patch, audit, or physically secure. Common risk factors include:
- Outdated or inconsistent firmware versions
- Insecure communication protocols
- Limited visibility into authentication and access behavior
From a monitoring perspective, security issues rarely appear as explicit failures. Instead, they surface as behavioral anomalies—unexpected traffic patterns, sudden data volume changes, or irregular reporting intervals.
Effective IoT monitoring must therefore track firmware state, authentication signals, and behavioral deviations, not just uptime or performance metrics.
Key takeaway: Without security-aware monitoring, IoT failures are detected too late—after impact occurs.
Reducing Noise and False Alerts
Alert fatigue is one of the fastest ways IoT monitoring systems fail operationally.
As device counts grow, even small error rates can generate thousands of alerts. Static threshold-based alerting becomes unreliable because “normal” behavior varies widely by:
- Device type
- Location and environment
- Time of day or season
- Network conditions
In large IoT systems, meaningful issues are rarely single-point failures. They emerge as patterns across devices and time.
To remain effective, IoT monitoring systems must:
- Correlate signals across multiple dimensions
- Favor trend- and pattern-based detection
- Reduce reliance on fixed thresholds
Key takeaway: Scalable IoT monitoring depends on detecting system-level anomalies, not individual signal spikes.
How to Choose an IoT Monitoring Platform
Choosing an IoT monitoring platform is less about finding a single “best” tool and more about understanding which architectural approach fits your system’s scale, data characteristics, and operational goals. As IoT deployments evolve, the gap between basic monitoring and system-level insight becomes increasingly clear, making platform selection a strategic engineering decision rather than a purely tooling choice.
Core Capabilities to Look For
When evaluating IoT monitoring solutions, prioritize:
- Scalable and flexible ingestion
- Low-latency, ad-hoc querying
- Support for high-cardinality and evolving data
- Integration with observability and analytics workflows
Architecture matters more than feature checklists.
When Traditional Monitoring Tools Fall Short
As IoT deployments grow, many teams find that traditional monitoring tools—built around predefined metrics and static dashboards—struggle to support exploratory analysis and system-level understanding.
At this stage, IoT monitoring begins to resemble observability more than traditional infrastructure monitoring, shifting the focus from individual signals to overall system behavior. In practice, some teams adopt observability-inspired architectures where telemetry data is stored and analyzed in real time.
Platforms like VeloDB are used in these scenarios to support both monitoring and interactive analysis on large-scale IoT data, especially when low-latency queries and flexible data exploration become essential.
People Also Ask About IoT Monitoring
What is IoT remote monitoring?
IoT remote monitoring refers to using connected devices to observe and analyze system behavior from a distance, without requiring on-site presence. It enables teams to collect telemetry from geographically distributed devices, transmit it over networks, and monitor performance, conditions, or anomalies in near real time.
In practice, IoT remote monitoring is most valuable in environments where devices are difficult, costly, or unsafe to access—such as industrial facilities, remote infrastructure, or large outdoor deployments. Technically, it relies on the same system-level principles as IoT monitoring, with additional emphasis on connectivity reliability, latency, and delayed or intermittent data.
What does IoT stand for?
IoT stands for Internet of Things, referring to networks of physical objects—such as sensors, machines, and embedded devices—that collect and exchange data over the internet or private networks. These devices typically operate with limited resources and are distributed across diverse environments, which introduces unique challenges for monitoring and data analysis.
What are the 4 types of IoT?
IoT systems are commonly grouped into four categories based on their use cases:
- Consumer IoT, such as smart home devices and wearables
- Industrial IoT (IIoT), used in manufacturing, energy, and utilities
- Commercial IoT, including retail, logistics, and fleet management
- Infrastructure IoT, supporting cities, transportation, and environmental systems
Each category differs in scale, data characteristics, and monitoring requirements.
Final Takeaway: When IoT Monitoring Makes Sense
IoT monitoring makes sense when device data becomes a core input to system behavior, rather than a byproduct of device operation. As deployments scale, monitoring shifts from checking individual devices to understanding how data flows, changes, and fails across the system.
Organizations benefit most from IoT monitoring when devices are widely distributed, data is consumed continuously, and latency or anomalies have real operational impact. At this point, IoT monitoring aligns closely with observability principles—focusing on system behavior instead of isolated signals.
If device counts are small and issues are easy to diagnose locally, full-scale IoT monitoring may add unnecessary complexity. The key is recognizing when system-level insight becomes essential.